Early proponents of the Internet of Things (IoT) took the centralized network approach that had worked so well within the comfortable confines of corporate IT and imagined it applied, unhindered, to hundreds, perhaps thousands of square miles of real-world geography.
Early proponents of the Internet of Things (IoT) took the centralized network approach that had worked so well within the comfortable confines of corporate IT and imagined it applied, unhindered, to hundreds, perhaps thousands of square miles of real-world geography.
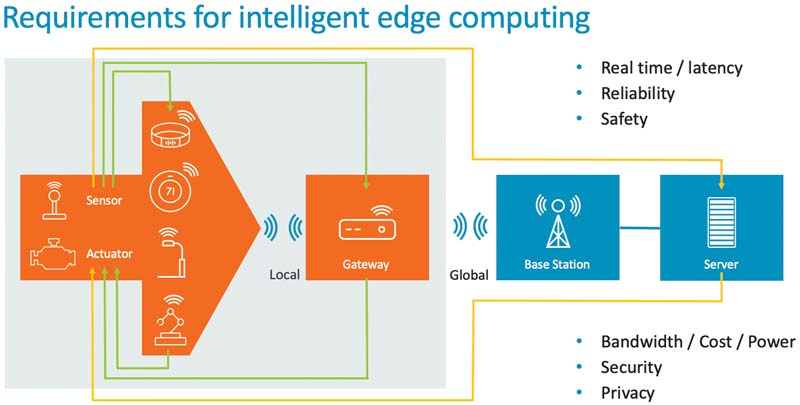
Yet in reality, the latency and vulnerability that topography and distance introduce stands to limit so many of IoT’s most interesting use cases. Applications first to fall are those in industries operating within challenging conditions such as oil and gas, remote healthcare and disaster relief. Next is any device for which an instantaneous response is vital – such as medical equipment or an autonomous vehicle. Even smart cities, which may seem far more fertile grounds for IoT proliferation, will struggle as the burden of big data defeats available bandwidth and the cloud’s ability to process at such scale.
 Overcoming the barriers of data and distance for IoT to scale
Overcoming the barriers of data and distance for IoT to scale
In 2016 the IoT generated 1.6 trillion gigabytes of data, and Cisco estimates this will rise to 500 trillion gigabytes by the end of 2019, growing exponentially in years following. As the data grows, the friction it encounters along its journey will increase.
If distance increases network latency, the obvious answer is to decrease the real-world distance between where sensor data is collected and where it is processed. This means enabling compute in the most physically appropriate location – whether that is on the device, in mid-network equipment such as a gateway or in the traditional cloud. Data will still travel from the edge to the cloud, but in the form of compact, computed findings rather than raw information.
Giving devices the power and resource to perform their primary function independently benefits a far broader spread of industries in tech-hostile environments, such as mines, oil rigs, underwater applications and other adverse environments that may lack the safety net of always-on internet connectivity – or even always-on electricity.
Ensuring security is built in low-power devices from the ground-up
Of course, there are other factors to consider: the level of compute, privacy and security required and how much latency can be tolerated. Increase the compute capability and complexity and cost and power consumption may skyrocket. Then there are the physical extremes: a wave-powered gas sensor placed on the bed of the North Sea needs to be able to perform, and to keep performing, its primary function – even if network or power connectivity is lost for long periods of time.
In terms of security, this requirement must run throughout the entire design process. We need a standardized, holistic, scalable security framework for low-power devices, such as the Arm Platform Security Architecture (PSA). It provides a common foundation, based on industry best-practice, that allows security to be consistently designed in at both a hardware and firmware level.
Arm TrustZone security technology takes it one step further to simplify IoT security and offer the ideal platform on which to build a device that adheres to PSA principles. All of this is possible with the Arm ecosystem of silicon partners, software, tools, OSes and resources, helping developers speed time to market.
The enablement of compute at the edge isn’t just one more step towards a world of a trillion devices; if we want to realize the global ambitions of the IoT, then we need the entire spectrum of compute capable, fired up and ready, from the smallest device to the highest performance data center.
Author: Chris Shore,
Director of Embedded Solutions at Arm
Learn more about IoT solutions from Arm
www.arm.com