The connected MCU
The connected MCU
Today microcontrollers (MCUs) are finding their way into nearly every application – in traditional areas such as industrial machinery and automotive to new areas such as wearables and even ‘smart’ clothing. More and more, MCU designs incorporate some kind of connectivity e.g. Bluetooth Smart, ultra-low power Wi-Fi, NFC and Zigbee. Connected MCUs must control their own states and resources, capture and process sensory data, perform some analytics and maintain secure storage; they must also communicate to a remote host for data transport, platform management, and OTA updates. With embedded applications growing increasingly sophisticated and connected, threats to embedded platforms are increasing significantly. Security must be an up-front design consideration, not an afterthought.
Within an MCU there are several methods to build security. This includes secure boot and secure code updates. In addition, CPUs with a Memory Protection Unit (MPU) can improve system security by preventing unauthorized access to boot code and execution of non-trusted kernel mode code.
Key protection and tamper resistance are other important security measures. Anti-tamper features can prevent external ‘snooping’ devices from reading the core memory and/or working out what code is executing – providing yet another layer of security against potential external attacks.
Another key security implementation method is to take advantage of hardware virtualization technology offered in some CPUs. With hardware virtualization it is possible to build a micro-controllers that can run multiple, unmodified, isolated applications independently and securely at the same time on a single, trusted platform. End customers can use this feature to provide a secure path to deliver updates/downloads, and benefit from enhanced IP protection.
Why Micro-virtualize
Hardware virtualization is commonly associated with server-class processor technology. It has been used on 64-bit server platforms for many years and is proven and widespread in the enterprise. Virtualization can enable consolidation of multiple similar or dissimilar workloads in datacenters to decrease capex (hardware and infrastructure costs) and opex (reduce power consumption, cooling), etc.
In an embedded platform, the use of virtualization is different; the primary purpose is to ensure security through separation. We define ‘security’ as the ability to isolate, police, and enforce behaviors on guest software. Such a technique enables consolidation of multiple different embedded CPUs into a single core resulting in lower silicon area and development effort, ultimately decreasing the overall cost and extending battery life.
It all starts with isolation. With virtualization, common resources on a hardware platform can be partitioned into logically separate environments referred to as virtual machines (VMs).
Each VM is comprised of applications and relevant operating systems (if required). Through hardware virtualization, it is possible to separate and protect critical assets such as communication interfaces (and software stacks), storage and other resources into their own address spaces, and ensure there is no access from/to any other applications’ address spaces.
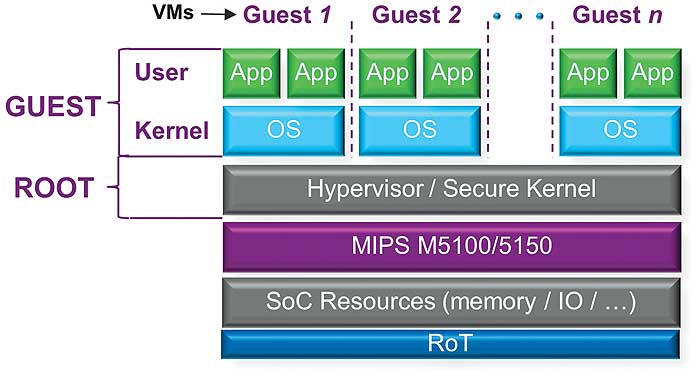
A simple view of virtualization in an embedded environment is shown in Figure 1. The MIPS M5100 and M5150 IP cores are small footprint CPUs with the ability to enforce isolation of up to seven Guests. In most of today’s embedded virtualized applications, up to three isolated environments is typical; the M51xx CPUs allow for future scalability. Once the critical assets are isolated from potential vulnerabilities, the next step in protection is implementing and ensuring trust for each isolated environment. A hardware Root of Trust (RoT) and associated security services can be used to enforce trust — both authentication and privacy. The virtualized platform is based on a trusted hypervisor, which creates and manages the VMs, executing at the highest privileged Root level of the processor – also shown in Figure 1.
The structural integrity of the hypervisor can be maintained by following a trusted boot process. The operational integrity is not compromised since the hypervisor runs in its own unique context provided by the hardware, and is isolated to its own address space. Each address space is protected by the root memory management unit (MMU); whose contents can be locked down immediately after boot to provide absolute isolation of all address spaces.
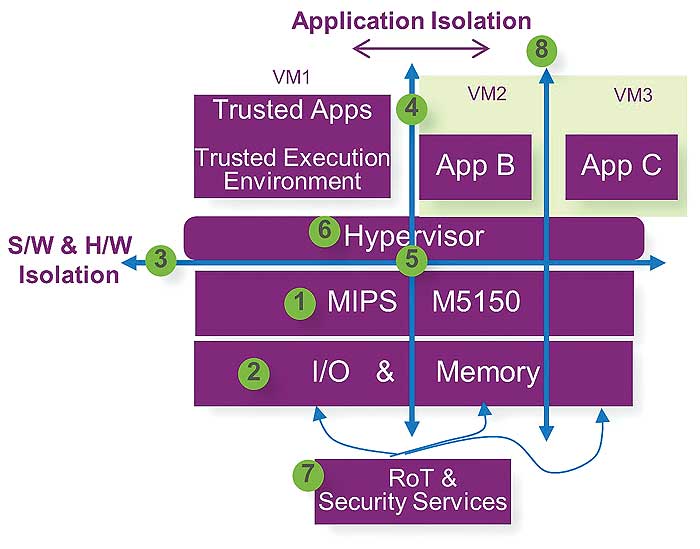
Figure 2 shows the potential benefits of virtualization in embedded applications. In this case, a MIPS M5150 CPU is configured to support up to three distinct isolated environments. Each environment is isolated and protected from the others, including memory and IO. Generally, the RoT and security services provided are assigned to the trusted environment. RoT security services requested by other environments (VM2 or VM3) are redirected and managed by the secured environment of VM1.
Building Trust in a virtual environment
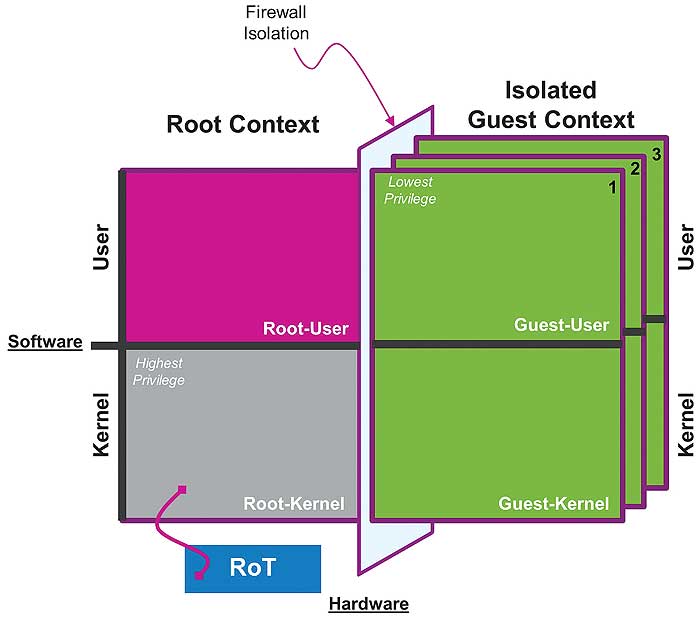
Figure 3 demonstrates the four quadrants required for creating security by separation and establishment of a trusted environment.
The MIPS M5150 can be divided into 4 areas / quadrants based on two axes. This is in contrast to the traditional single axis operation of User and Kernel space. The User and Kernel spaces are grouped into Root and Guest context.
Guest-User: user land with lowest privileged state where rich applications are generally executed
Guest-Kernel: typical kernel space of a CPU where privileged OS level tasks are executed. Examples are Linux; Input-output, interrupt handling and memory allocation.
Root-User: a single privileged state of the CPU that can executed protected applications
Root-Kernel: The highest privileged execution state of the CPU where privileged instructions execute. Exceptions from violation can be handled in this state. Second level memory management is used to enforce protection of resources are also managed at this state. A trusted hypervisor can manage the operation of trusted applications and all other protected Guests.
Both Guest-User and Guest-Kernel can be replicated to create multiple isolated domains.
The Guest contexts are replicated into parallel domains or environments, each isolated by a hardware mechanism. In the case of the M5150, up to seven Guest contexts can be established bringing the total number of contexts to eight.
The Root context executes at a privileged state in the M5150; this allows privileged instructions, software routines, interrupts and exceptions to execute within this context, providing a mechanism for control, management and termination of Guest services as needed. Accesses from any Guest to Root resources can be prohibited by hardware. However, the Root context may act as a proxy to provide indirect access to restricted or protected resources.
The Root context can maintain an isolated state; however, to establish and maintain trust, an RoT can be implemented to start the SoC after power-up into a known state. The complexity of the RoT may vary from application to application and is a function of the attack and protection profile.
Dual-core features in a single core footprint
In addition to providing a basis for security by separation, hardware virtualization can provide other significant benefits for MCUs. In an embedded device, hardware virtualization can be used to reduce CPU overhead, dynamically allocate CPU bandwidth per application, increase hardware utilization and provide more flexible system management.
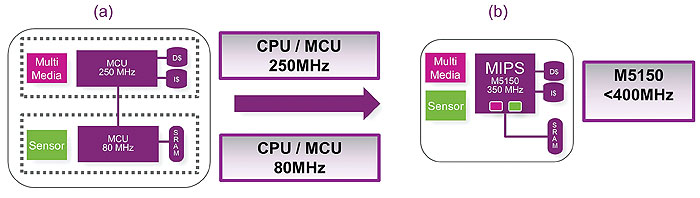
For many industrial, connected home and connected vehicle applications, it is possible to save costs by replacing multiple CPU cores with a single core. Dual-core MCUs are typically targeted at applications that have a mixed use case situation, Figure 4(a). One lower-performance core is targeted at lower-level functionality such as sensor control while another higher performance core manages the more complex tasks for audio processing or other multimedia applications. This type of configuration can be seen in many wearable, IoT and embedded applications.
The use of a single core allows the tasks to be managed with separate resources in both memory and IO, enabling separation of tasks without the added complexity of dual cores, Figure 4(b). The additional performance also gives more flexibility to scale to new applications without the fixed limits of the dual-core partitions. In comparison to competing dual-core embedded CPUs, a single-core MIPS M5150 offers a performance boost of up to 35%, while lowering area by as much as 10%, resulting in more efficient operation. The single virtualized core design reduces complexity, interconnect and debug time, and improves security and flexibility.
Use case
An IoT node device must handle multiple security requirements, including trusted boot, trusted and secure operation and communication – just to name a few.
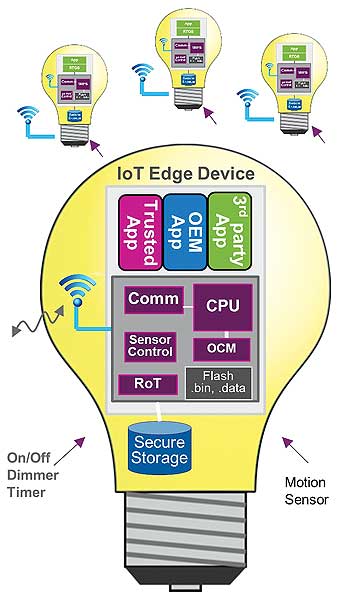
Hardware virtualization allows the flexibility of implementing a solution that can scale and adapt to the requirement of the IoT node device while maintaining the overall cost of implementation, validation, certification and operation of the device. In Figure 5, the trusted application handles all the security related tasks such as control of the sensors while capturing, processing and storing sensitive data; separately establishing secure communication to the host, either locally or over the cloud. The OEM application maintains isolation from any third party applications. For a third party application, being deployed in its own environment simplifies validation, deployment, and revocation while providing another level of security for the base services.
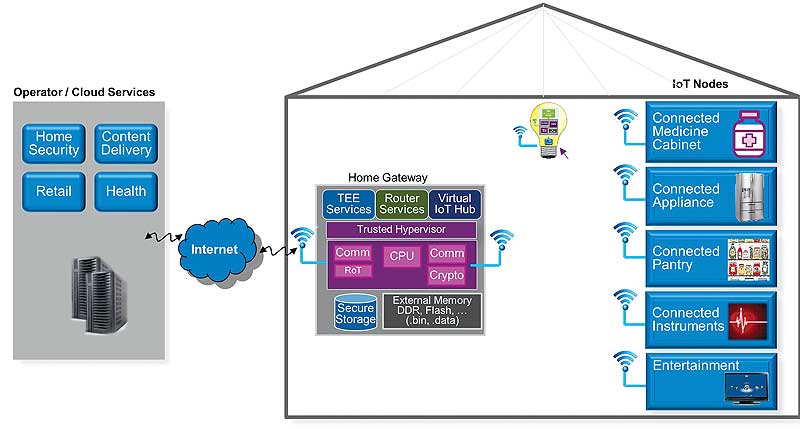
In a connected home environment (like that shown in Figure 6), there are many distinct IoT node devices that must securely be provisioned and managed by remote trusted service providers under the supervision of the home owner.
Conclusion: Embedded Security by Separation
Security is critical to the successful and safe deployment of connected devices in the smart home and city, industrial environments, automotive applications, wearables and many other areas. Security fundamentals require that we use a trusted operating environment enabled via a Root of Trust that is impervious to attack – leveraging a root of trust engraved in hardware, which is the basis for establishing a chain of trust for all subsystems.
Security by separation enabled by hardware virtualization provides an additional layer of trust by ensuring that applications and guest OSes are kept separate from each other. Separating the Guests running in VMs from the real hardware and isolating VMs from each other provides a strong foundation for security through enforced isolation, with the hypervisor as the high-privilege base for security services; provisioning security services per VM. This implementation can keep user and application data separate from each other to secure against external hacking, keep certified software away from user edits, and isolate communications interfaces and user application software for better internal security / data privacy.
Such an implementation must go beyond a binary approach (one secure zone/one non-secure zone). The minimum implementation in a connected device would ensure separate, isolated environments for the critical device assets, communication interfaces and the software stack running them, storage and other resources in the system.
Imagination’s OmniShield multi-domain separation-based architecture can scale far beyond a binary world, enabling each secure or non-secure application to exist in its own isolated environment where it operates independently. Implemented in many MIPS CPUs including the MIPS M5100 and M5150 IP cores, OmniShield provides a foundation for trust that is a growing concern in connected devices – including tomorrow’s microcontrollers.
by Majid Bemanian
Imagination Technologies | www.imgtec.com