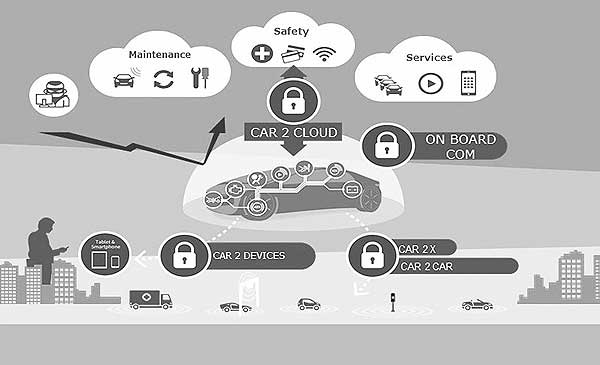
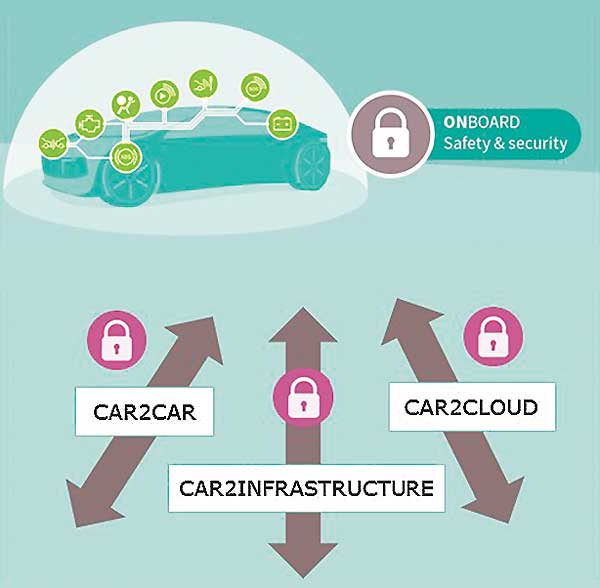
The importance of vehicle cyber security is growing due to the increasingly dominant role of the Internet and remote applications as well as the trend towards fully autonomous vehicles. Although cyber security is well known as a part of daily routines in the traditional IT sector, it is not yet widespread practice in the automotive industry. At first glance, this appears to be a minor problem as there is an array of solutions from other sectors that could possibly be used for vehicle safety. However, the automotive-specific environment makes this further use somewhat difficult.
Today, customers expect the unlimited availability and networking of smartphones and other personal mobile devices in automobiles, as well as the application of cutting-edge satellite navigation systems with a high demand on the quality of the display and the density of information – in short, complete networking. A constant data connection with an external infrastructure or external devices will also be needed in the future. Vehicles will thus become a target for cyber-attacks and other manipulation. The focus is therefore certainly on guaranteeing confidentiality, integrity, and authenticity – which will ultimately require additional protective measures. The various communication units – from OEM backend system to the vehicle and within the individual control units (ECUs (Electronic Control Units)) – demand secure authentication and protection against data manipulation. To guarantee this, encryption key-based cryptographic methods are used for communication. An encryption process is basically a cryptographic method that uses an encryption key to convert plain text into cipher text which can then be translated back into plain text using a cipher key.
The non-disclosure and protection of these encryption keys are – besides other factors – a fundamental requirement for the security architecture. Because if the availability and confidentiality of the keys are breached, overall security is compromised. The impacts on the automotive industry might be disastrous – and potentially fatal to its finances and extremely damaging to its reputation. If attackers know the relevant keys, they can influence the communication. In other words, the vehicles would need to be taken to a secure environment (workshop or even factory), which is stressful and costly in terms of both time and money.
Against this background, the non-disclosure and protection of the archived keys are essential for cyber security and fully functional security (pursuant to ISO 262262) in cars.
Trust anchors
Hardware-based trust anchors can be used to protect archived encryption keys. In this case, measures must be taken to ensure only the authorized entity has sole access to the encryption service of the trust anchor. The trust anchors represent a secure, isolated environment in which the keys and certificates are saved and processed. A number of hacker attacks have clearly demonstrated that implementation of these trust anchors in software (as part of the microcontroller operating system) is inadequate.
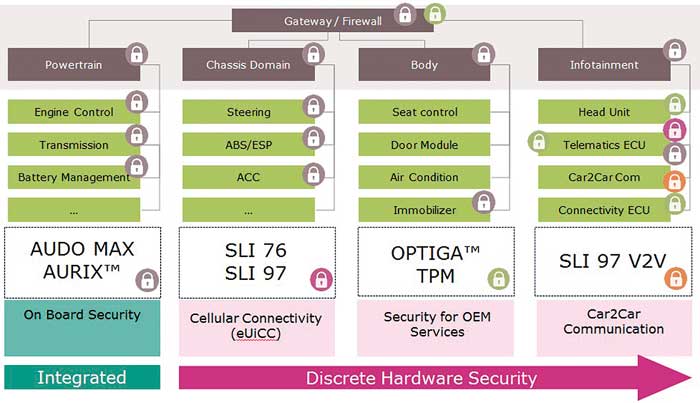
Integrated on MCU (HSM)
▶ Onboard security
▶ Protected com. & debug interfaces
▶ High-speed/real-time critical tasks
Discrete Security Controller
▶ Protected external communication
▶ Certified hardware security
▶ Protecting critical keys & certificates
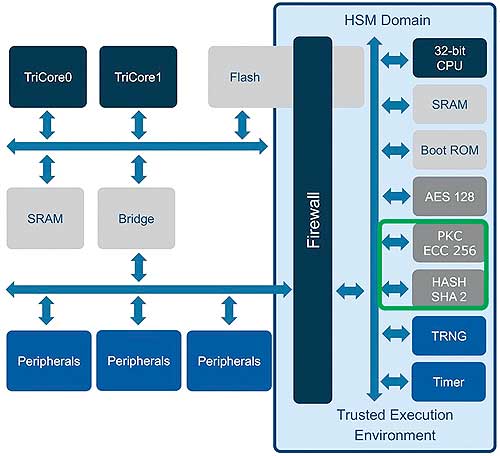
The HSM (Hardware Security Modules) in AURIX™ microcontrollers are used as trust anchors and isolate security functions from the other functional units of the microcontroller.
Implementation of dedicated hardware offers more effective and better protection. Based on these facts, SHE (Security Hardware Extension) modules and HSMs (Hardware Security Modules) were developed and integrated into microcontrollers. The Infineon AURIX™ microcontrollers have, for instance, an integrated HSM, with second generation HSMs (TC3xx) additionally supporting asymmetric cryptography (key pair consisting of a private and public key). Particularly efficient protection, especially for security-critical areas, such as outward vehicle communication or the infotainment sector, is offered by special security controllers like OPTIGA TPMs (Trusted Platform Modules). The TPM guarantees secure authentication. To achieve this, it stores utilized certificates and relevant keys long-term in a protected environment.
Various functions are implemented in the hardware-based trust anchors to protect security-critical processes and, for example, the transfer of keys. In this respect, the functional complexity (the code) is, in comparison to the controllers being protected, relatively small. The reduced complexity enables comprehensive testing of the hardware and software, which is not financially feasible for an entire system.
The use of microcontroller (HSM), TPM or SIM-based solutions as trust anchors in cars is determined by the respective application. Implementation via HSM (integrated in the microcontroller) is basically aimed at in-vehicle communication, which demands a high level of computing performance and a robust real-time behavior. Conversely, special TPM controllers secure the external communication, which poses a higher risk for cyber security. Furthermore, they can be used as the main storage for security-critical keys and certificates. They also offer protection from so-called side-channel attacks. These analyze, e.g., the runtime of the algorithm, the electric power being consumed by the processor during the calculations or the electromagnetic emanation to divulge information about the keys.
The following principles apply to data security in automobiles:
• The integrity of electronic keys is a major factor for the data security of an electronic system.
• It is impossible to achieve a sufficient level of data security with manipulated or easy-to-manipulate electronic keys.
• Cloned electronic keys do not leave any traces.
• Secure handling of electronic keys must be guaranteed throughout a product’s entire life cycle.
• Trust anchors enable key administration and application in an insecure environment (e.g. during vehicle operation).
Efficient protection through standards
In the meantime, car makers classify data in terms of their security relevance. The respective classification also impacts the required measures or the justified protection for the corresponding keys. The lifespan of electronic keys is relevant as well. Electronic keys with a higher demanded lifespan offer greater protection than electronic keys that can only be used for a limited period (session keys). The actual reuse of established, widespread algorithms and procedures for security mechanisms and implementation reduces the level of specific effort related to vehicle data security. After initial negative experience using in-house developed proprietary algorithms, standardized encryption techniques, including AES, RSA, and ECC, have become the norm in the automotive industry.
Although the re-application of existing and proven security technologies is desirable, cars have other specific requirements that need to be addressed: Cars need to meet higher quality standards under robust operating conditions, offering greater reliability and above average life expectancy. Data security solutions from the world of chip-card technology are already in widespread use. In terms of their application in vehicles, an extended temperature range and common qualification standards also need to be considered – an example of security controllers in this respect is SIMs. The automotive industry therefore relies on robust, solder-able SIM technologies to meet requirements in terms of vibrations, extended temperature range, and the automotive standard AECQ-100.
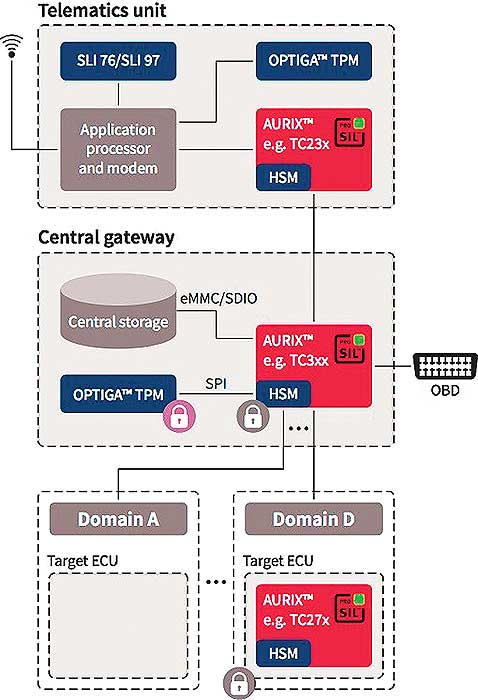
Microcontrollers with HSM and TPM security controllers offer, for example, hardware-based security mechanisms for the various functions of a SOTA application within the vehicle.
Full life protection
The encryption keys used in cars must, depending on the key management and techniques, be protected throughout the vehicle’s entire life cycle, from production and use through to disposal. Production is a particularly critical phase within this process. As this is the point where keys must be transferred in plain text. If this process is not protected adequately, attackers can gain access to a large number of keys. Further, key injection may be performed at several locations and by subcontractors, which puts greater pressure on security processes and resources. An efficient solution is the application of a personalized security controller. Personalized in this case means the security controller has an individual personal key allocated to the chip which was stored by the semiconductor manufacturer during a certified manufacturing process. Seeing as these security controllers are protected from hardware attacks, they can be supplied without any special logistic requirements. Since they can only be manipulated using the personalized key. A personalized security TPM controller additionally facilitates the personalization process of the control devices, as the protected private key in the controller can be used to transfer further keys via secure communication.
The safety of a product depends on the quality of the security processes and should play an integral part in the product development and production phases. For instance, the development and production process of the OPTIGA TPMs is certified to Common Criteria. The current version of the Common Criteria was issued in 1999 as the international standard ISO/IEC 15408 and specifies the criteria for evaluating and certifying the reliability, quality, and trustworthiness of IT products. Furthermore, the TPMs are produced and personalized using manufacturing processes that are also fully audited and certified. This strict monitoring of security processes by independent or state-approved certification bodies is the foundation for the high level of security quality provided by Infineon’s TPMs. Another critical factor is the long life expectancy of vehicles of up to 20 years or more. A further demand is that the implemented crypto algorithms are also secure throughout the vehicle’s entire service life. To enable this, the security architecture should facilitate simple crypto functionality switchover, possibly support both old and new algorithms in parallel, and offer sufficient hardware resources (buses, memory, etc.) for new, longer keys. This so-called “crypto agility” is supported, e.g., by the TPM 2.0 standard.
Example of SOTA application
Costly recall actions to eliminate software problems in vehicle control units have forced car makers to increasingly consider the opportunities that would arise from performing software updates over the air (SOTA). Besides the saved callback costs, the mobile connection to the vehicle and the option to download new software via this communication interface enable new functions and applications. Dedicated security solutions provide hardware-based security mechanisms for various functions in a SOTA application within the vehicle.
In addition to end-to-end communication between OEM server and target control unit, the vehicle architecture for SOTA can be implemented via three control units (ECU blocks) where different security solutions assume the respective security functions: Telematics control unit, central gateway, and target control unit. The authentication and encryption services are activated in the telematics unit using the wireless connection and the transmitted data (from the OEM) are then received and decrypted using a secure protocol. The implementation of a dedicated TPM security controller is recommended for this critical authentication function to protect the security-critical keys and certificates. Subsequently, the software update is stored in the vehicle’s main memory. After OEM authentication and verification (in the central gateway), the respective data packages are unpacked for the control units. The actual update process with programming then commences and the data packages are sent in small blocks to the ECUs. Within the ECUs, the data blocks are decrypted, decompressed, and a new code is written in the flash memory of the target control unit via the secure flash bootloader. The secure flash bootloader is a key element for the SOTA process within the control unit. The main security functions are, for instance, executed by the HSM in the AURIX™ microcontroller: Secure booting, authentication, decryption and encryption, key management, and integrity check. Authentication for flash access prevents unauthorized read and write access to the flash memory. Flash access is only enabled by the HSM after successful authentication of the central gateway and after sending a respective programming command. After successful verification of the update, this is reported to the update server. At the end of the update mode, the vehicle is rebooted or started with all the ECUs.
Conclusion
State-of-the-art semiconductor solutions enable vehicle security systems with high functional security and cyber security that protect the vehicle as well as car and road users. Optimized for specific applications, 32-bit microcontrollers with integrated hardware security modules (HSM), SIM controllers, and special TPM security controllers, as well as corresponding software packages are available. This way it is possible to adapt the respective security mechanisms to the security requirements of a particular application. Utilization of proven crypto algorithms, e.g. AES and ECC, as well as adherence to standards, e.g. SHE, EVITA, and TPM, minimize the risk and the integration effort for OEMs, their suppliers, and sub-suppliers.
Author: Martin Motz, Product Manager CPU
Rutronik | www.rutronik.com
![]()